Faraday is the Integrated Multiuser Risk Environment you were looking for! It maps and leverages all the knowledge you generate in real time, letting you track and understand your audits. Our dashboard for CISOs and managers uncovers the impact and risk being assessed by the audit in real-time without the need for a single email. Developed with a specialized set of functionalities that helps users improve their own work, the main purpose is to re-use the available tools in the community taking advantage of them in a collaborative way!
Data Analysis tools
Since Faraday allows you to keep all of your pentests in one place, we thought it would be interesting to add the possibility to see your assessments come to life, so we added new data analysis reports to the Web UI:
- Tools findings by severity and targets
- Vulnerability severity cluster
- Severity timeline
- Service vulnerability timeline
- Target severity pie charts
- OS severity pie charts
- Severity by tool boxplot
- Total vulnerability correlation with price by each OS
- Vulnerability by type chart, ease of resolution and OS
- Vulnerability by year tree
These charts allow you to find new relations between your data and clarify the state of an assessment.
We will also add new charts in the future, and the possibility to customize them as well!
As an example, this is how some of the current reports look
Target severity

Vuln severity price vs creator

Target severity cluster map

Tools findings by severity and targets alluvial chart
You can also download the charts as
PNG or
SVG format to include them in your custom reports.

Download charts as PNG
Credentials CRUD
One of the big goals in every internal pentest is gathering service credentials to
log in to a host, escalate privileges and pivot. Wouldn’t it be great if you could store all your credentials in one place? Now you can!
Save all the found creds in Faraday’s DB, query it using the
Faraday Plugin and feed other tools to keep hacking!
Vuln templates CRUD
Manually creating vulnerabilities has always been a nuisance, from getting evidence to wording the descriptions - no one likes it. And also, explanations vary between testers, so what sounds perfectly understandable to one person can be gibberish to another.
Knowing this is a continuous issue when reporting, we added the
Vulnerability Templates Database in version 1.0.12. We knew back then that editing a
CSV and uploading it every time a change was needed wasn’t the best approach, but other features came first when prioritizing.
An improvement on this feature was long overdue so we created a brand new view in the Web UI just to manage these templates. You can now upload a CSV file from the Web UI and then edit the templates as desired.

Vuln templates view
But wait! The plot thickens! You can also create a template from an existing vulnerability!
Write your vulns once, and use them forever.
Hosts revamp
When users wanted to edit or create hosts in previous Faraday versions, the only options was through a modal dialog. This was especially annoying in small screens, when scrolling and cluttered information became a hassle.
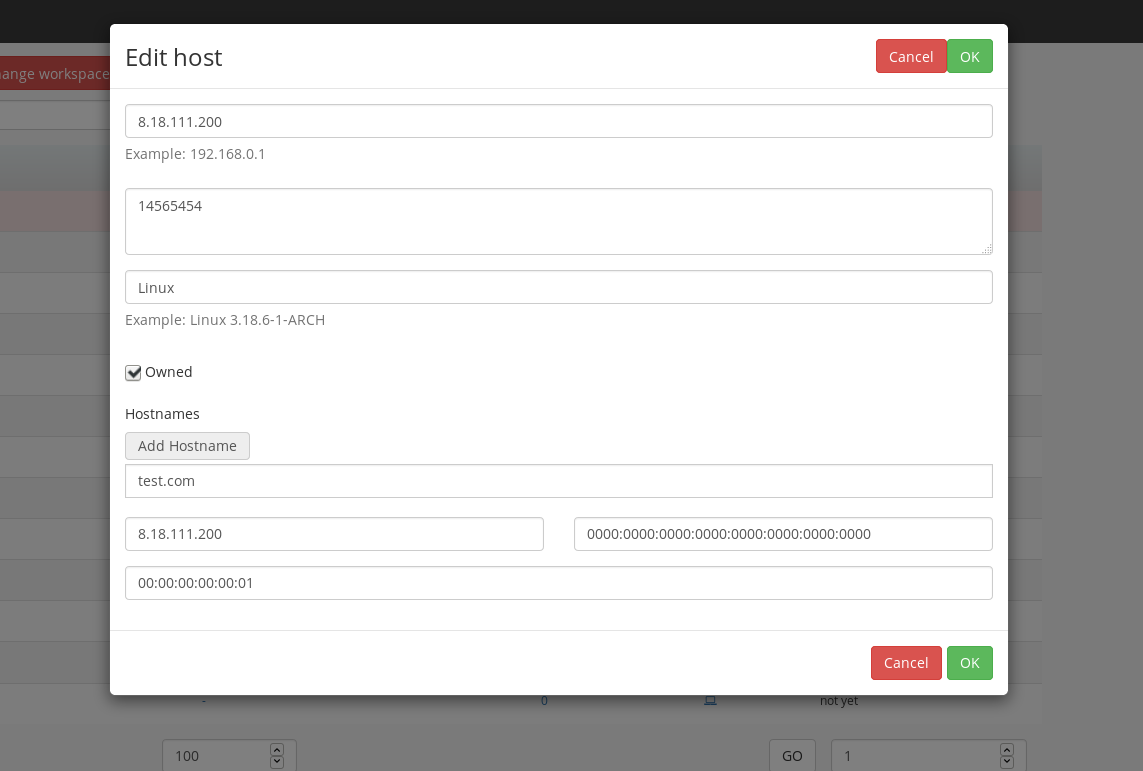
Deprecated modal view
Keeping in mind that managing hosts is a very important task to pentesters and managers alike we decided to update the hosts manager. As of this version you can
examine, create and edit hosts from the same full view. Since it is no longer a modal dialog, the whole browser window is used, allowing to have all of the host details, along with its services in plain sight.
No more scrolling, no more three clicks to get the host info!
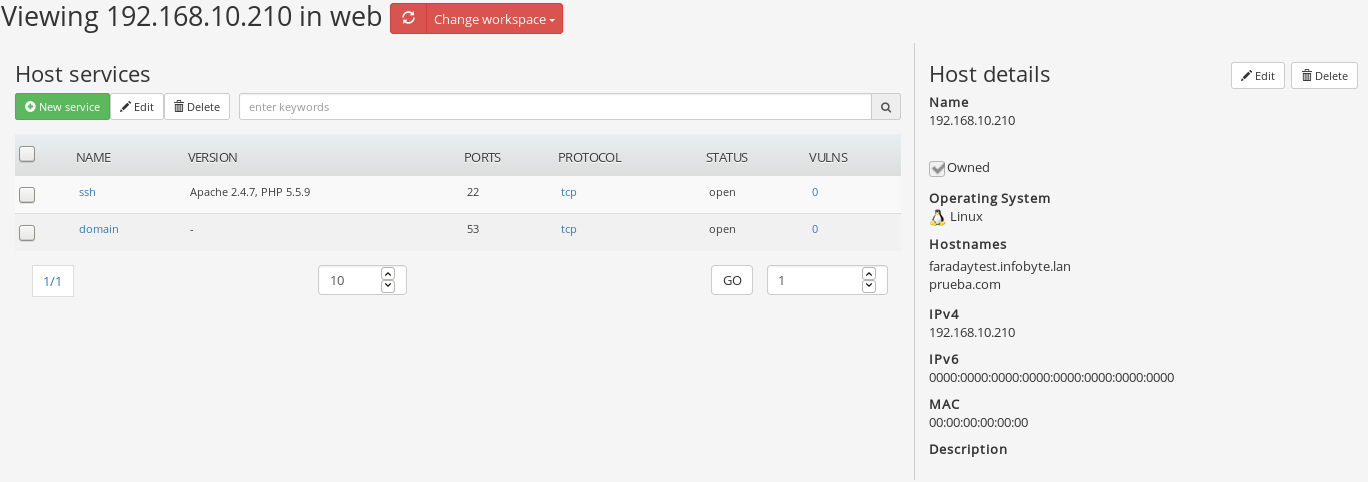
Improved host view

Host creation view
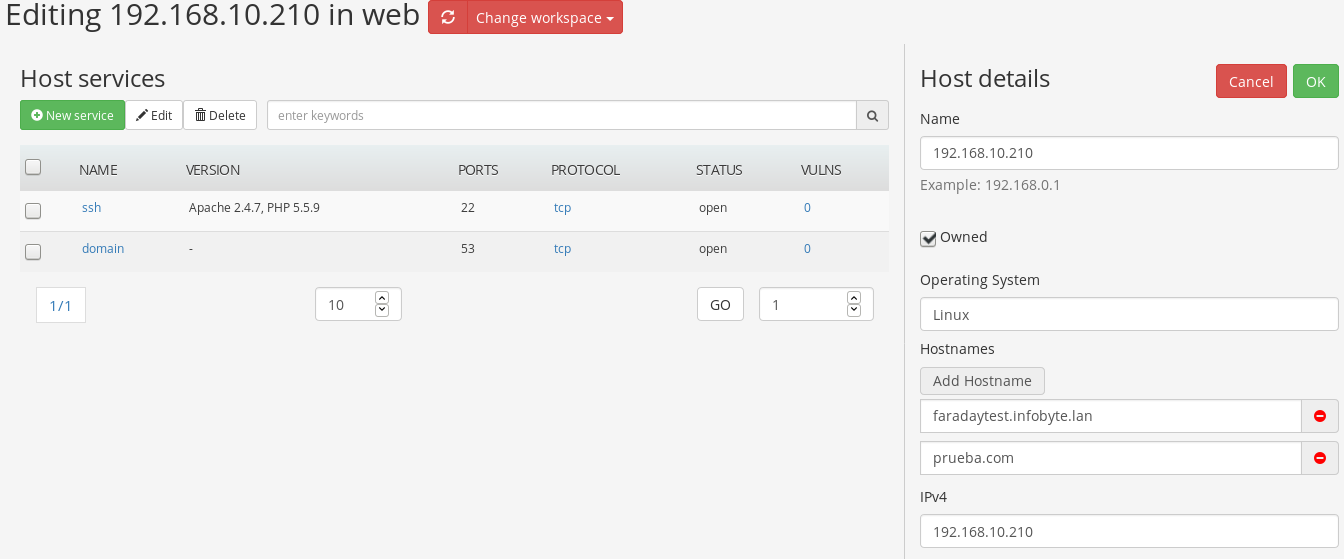
Host edition view
Plugins Core Improvements
Faraday’s Plugin System is a core piece of the platform and that is why we constantly work on adding new tools and improving the ones we already support. In this iteration we improved the system itself so that plugins can access the error console and communicate with the user in a simplified manner.

Plugin output
On the maintenance side,
we fixed a bug in the Nessus plugin which locked the vuln edition after processing and added support for
SQLmap‘s -r argument that allows adding an HTTP request file instead of manually loading the URL and headers. We also modified a few other plugins (Core Impact, Netsparker, Nikto, Propecia, Qualysguard, SQLmap, Telnet and Wapiti) to improve the content of the vulnerabilities that are added to the platform, creating better Executive Reports.
Misc
It’s not uncommon for our users to switch between versions (for example, when upgrading from Community to Pro) and some issues arose in that process. Keeping that use case in mind, we improved how the Faraday Client verifies its version against the Server to avoid further issues in the future.
Also, we did some improvements in GTK’s link to the Web UI and corrected a bug that prevented the Web UI from saving changes to workspaces created using the GTK Client.
Some of our Pro and Corp users had troubles starting the Server with no internet connection. We changed its behavior when bootstrapping without an active internet access, allowing users to run it even with limited connectivity.
Regarding the Executive Report, we fixed a minor bug that generated inconsistent reports when grouping regular vulns with web vulns.

Target, website, param name and path are grouped correctly
With the new additions to the Web UI, the left navigation bar was overloaded so we removed the administrative links (Workspaces, Users and Licenses) and added them to a new admin menu on the top right, along with a link to the Help page and an about dialog.

About Faraday
A special config for our Corp Customers
Because of a refactor in the auth system made in the last Corporate Version Release we need to ask the users to setup CouchDB correctly to avoid constantly losing the session.
To avoid headaches, follow this step-by-step guide:
- Turn off Faraday Server (./faraday-server.pyc –stop)
- Turn off CouchDB (systemctl stop couchdb)
- Modify the file “local.ini” usually located in the path /etc/couch/local.ini
- Add the following lines to the [couch_httpd_auth] part of that file
allow_persistent_cookies = true
timeout = 9999999
- Initialize CouchDB and Faraday Server again and you are all set
Changes and fixes
Corp changes
- Added a Data Analysis component to the Web UI
Pro & Corp changes
- Fixed a bug in the GTK interface when trying to configure an non-existent URL
- Always redirect to login page when user is not logged in
- Prevent users with role client to login using GTK
- Disable host and vuln edit buttons when logged in as client
- Fixed the server, which was refusing some valid licenses
- Improved grouping in Executive Reports
- Redirect to home page when a logged user visits login page
Community, Pro & Corp changes
- Fixed bug when editing workspaces created in GTK
- Improved host search in the WEB UI
- Extended the config to support different searching engines in the WEB UI
- Check that client and server versions match when connecting
- Adds the 'v’ and 'version’ argument for both the server and the client
- Fixed “refresh” button in the Web UI
- Fix API on /ws/<workspace> with duration object None
- Added a CRUD for Credentials to the Web UI
- Bug fixes on the Burp Online Plugin
- Added a script to connect with Reposify
- Fixed Hostname import in Nessus Plugin
- Make plugin methods log() and devlog() work again
- Fixed bug in SQLMap plugin that made the client freeze
- Improved SQLMap plugin to support more options and to show errors in GTK log console
- Fixed bug when creating/updating Credentials
- Improve plugins usage of vulnweb URL fields
- Fixed order of Report Plugins in the GTK import list





















